
Unit 8200 (2017)
A story about the world's best Cyber spies. Their training in Israel's military, and their impact on the world we live in.

A story about the world's best Cyber spies. Their training in Israel's military, and their impact on the world we live in.

The World's first cyber-sitcom. Whether you are a PC rookie or an experienced user looking to upgrade, this hilarious how-to readies you for Windows 95. Created with Microsoft, the Windows 95 Video Guide is your ticket to personal computing in the 21st century. And who better to drive you than Jennifer Aniston and Matthew Perry, TV’s hottest comedy stars as they go interactive with a cast of wacky propeller heads. Along the way, they’ll download essential instructions and give you the inside information. Plus, Microsoft answers The 20 Most Asked Questions about Windows 95. It all comes together for an eye-opening and entertaining instructional that gets you totally wired for Windows 95!
In 1900, a storm blew a boatload of sponge divers off course and forced them to take shelter by the tiny Mediterranean island of Antikythera. Diving the next day, they discovered a 2,000 year-old Greek shipwreck. Among the ship's cargo they hauled up was an unimpressive green lump of corroded bronze. Rusted remnants of gear wheels could be seen on its surface, suggesting some kind of intricate mechanism. The first X-ray studies confirmed that idea, but how it worked and what it was for puzzled scientists for decades. Recently, hi-tech imaging has revealed the extraordinary truth: this unique clockwork machine was the world's first computer.

This short documentary is a portrait of the early era of computing and the process and implications of the digitization of large amounts of information. Examining the arduous work of assessing and documenting the geographical landscape, including sampling and analysis of soil, forestry, timber, wildlife, resources, industrial sites, and many other aspects, we see that human beings alone couldn't handle the vast amount of information that is collected. A new kind of computer (an “instant library”), the Canada Land Inventory Geo-information System, was developed to help manage and develop Canadian land. This film examines the workings of this new and mysterious machine.
"Give me ten million dollars and trust me, we'll deliver a low-cost microprocessor compatible with Intel". This was former IBM Fellow and Dell Senior VP Glenn Henry's 1995 pitch to start a microprocessor company focused on low-cost Intel-compatible processors ("x86"). This documentary follows Henry and his team as they race to complete their latest chip, and offers an inside look at Centaur's unique management environment.
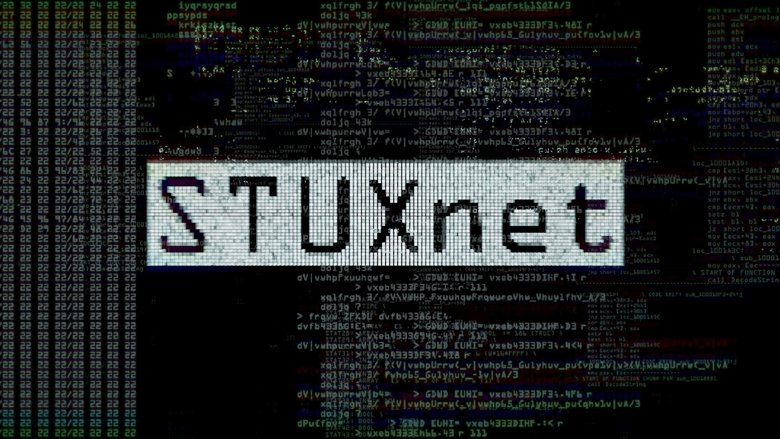
Alex Gibney explores the phenomenon of Stuxnet, a self-replicating computer virus discovered in 2010 by international IT experts. Evidently commissioned by the US and Israeli governments, this malware was designed to specifically sabotage Iran’s nuclear programme. However, the complex computer worm ended up not only infecting its intended target but also spreading uncontrollably.
OWNED presents the 50 year history of the law-spurning tech tradition of hacking. This vibrant movement gained momentum in the 1960s with Captain Crunch and phone phreaking and now includes annual DefCon hacker conventions in Las Vegas (an amusing highlight of these is the fun game "Spot the Fed"). Kevin Mittnick, dubbed by the New York Times "FBI's Most Wanted Cybercriminal" speaks for the first time about the crimes that lead to his conviction. Misanthropic hacker Fuqrag casually wreaks havoc on government websites from a claustrophobic trailer in an anonymous trailer park.
The onset of the 21st Century will be an era in which the very nature of what it means to be human will be both enriched and challenged as our species breaks the shackles of its genetic legacy and achieves inconceivable heights of intelligence, material progress, and longevity. While the social and philosophical ramifications of these changes will be profound, and the threats they pose considerable, celebrated futurist Ray Kurzweil presents a view of the coming age that is both a dramatic culmination of centuries of technological ingenuity and a genuinely inspiring vision of our ultimate destiny.

Exploring America’s consumption of computers and the hazardous waste we create in pursuit of the latest technology, Terra Blight traces the life cycle of computers from creation to disposal and juxtaposes the disparate worlds that have computers as their center. From a 13-year-old Ghanaian who smashes obsolete monitors to salvage copper to a 3,000-person video game party in Texas, Terra Blight examines the unseen realities of one of the most ubiquitous toxic wastes on our planet.
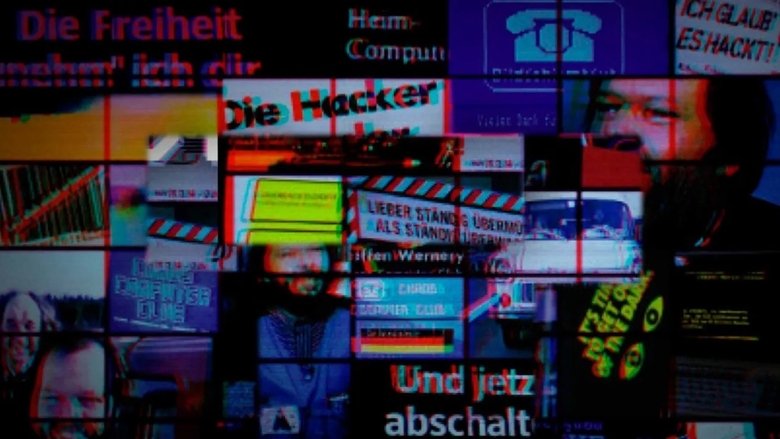
In 1981, Wau Holland and other hackers established the Hamburg based Chaos Computer Club (CCC). The idiosyncratic freethinkers were inspired by Californian technology visionaries and committed themselves to hacker ethics. All information must be free. Use public data, protect private data. But not everyone followed the rules. Computer technology was still in its infancy and the emerging Internet became a projection screen for social utopias. What has become of them? The story of the German hackers, told by the protagonists themselves in a montage of found video and audio material.

A desktop documentary about the online afterlife of the late French filmmaker, Chris Marker.

Explore how in the past five decades, the internet has changed the very fabric of our society, highlighted by interviews with the founders of AOL, Craigslist, Friendster, Match, and Tinder.

This behind-the-scenes documentary features interviews with the creators and cast of the cult comedy "The IT Crowd", plus chats with celebrity fans.
Six young women programmed the world's first all-electronic programmable computer, ENIAC, as part of a secret US WWII project. They changed the world, but were never introduced and never received credit. These pioneers deserve to be known and celebrated: Betty Snyder Holberton, Jean Jennings Barik, Kay McNulty Mauchly Antonelli, Marlyn Wescoff Meltzer, Ruth Lichterman Teitelbaum, and Frances Bilas Spence.

Does privacy still exist in 2019? In less than a generation, the internet has become a mass surveillance machine based on one simple mindset: If it's free, you're the product. Our information is captured, stored and made accessible to corporations and governments across the world. To the hacker community, Big Brother is real and only a technological battle can defeat him.

"Welcome to Macintosh" is a documentary that mixes history, criticism and an unapologetic revelry of all things Apple. Whether a long time Mac fanatic or new to computers, Welcome to Macintosh explores the many ways Apple Computer (now Apple, Inc.) has changed the world, from the early days of the Apple-I to the latest the company has to offer.

The Secret History of Hacking is a 2001 documentary film that focuses on phreaking, computer hacking and social engineering occurring from the 1970s through to the 1990s. Archive footage concerning the subject matter and (computer generated) graphical imagery specifically created for the film are voiced over with narrative audio commentary, intermixed with commentary from people who in one way or another have been closely involved in these matters.

What is Bitcoin? With the advent of Bitcoin, the world's first digital currency, for the first time in history money is no longer controlled by banks or governments, but by the people who use it. But where did this currency come from? How does it work? And is it truly the way forward, or just a flash in the pan? Magic Money answers these questions and more as it explores the mysterious origins of Bitcoin, its role in society, and how it could shape the future.

Documentary film investigating allegations of election fraud during the 2004 U.S. presidential election. Electronic voting machines count approximately 90% of America's votes in county, state and federal elections. The technology is also increasingly being used across the world, including in Canada, the United Kingdom, Europe and Latin America. The film uncovers incendiary evidence from the trash cans of Texas to the ballot boxes of Ohio, exposing secrecy, votes in the trash, hackable software and election officials rigging the presidential recount.Ultimately proving our votes can be stolen without a trace "Hacking Democracy" culminates in the famous 'Hursti Hack'; a duel between the Diebold voting machines and a computer hacker from Finland - with America's democracy at stake.
In 1986, astronomer turned computer scientist Clifford Stoll had just started working on a computer system at the Lawrence Berkeley Laboratory when he noticed a 75-cent discrepancy between the charges printed by two accounting programs responsible for charging people for machine use. Intrigued, he deduced that the system was being hacked, and he determined to find the culprit. This is the re-enactment of how he tracked down KGB cracker Markus Hess through the Ethernet to Hannover, Germany.